4 Enhancements to Elevate Your Splunk Platform
Still winding down from the incredible experience at .conf24, where we delved into the latest market trends, we’ve uncovered several fascinating enhancements for the Splunk platform. These improvements not only elevate the performance and efficiency of Splunk but also offer exciting features that will be available in future releases. Join us as we explore four powerful upgrades that can be used in your Splunk environment.
Foreach function enhancements
One of our favourite commands in Splunk is foreach, which enables you to run a subsearch using a template to iterate over multiple elements. Before Splunk 9.x, foreach could only be applied to a single value within a field. Let’s dive into an example to see how this works in practice.
The following query will simulate a data source which counts the attacks from different locations:
Unset
| makeresults count=5
| fields - _time
| eval attacks_external=10, attacks_internal=1, total=0
| streamstats sum(attacks_external) as attacks_external sum(attacks_internal) as attacks_internal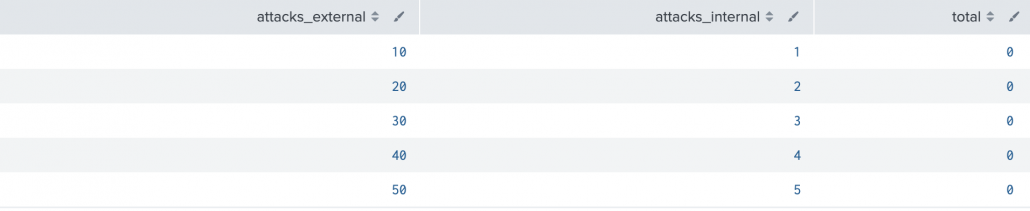
Now, let’s use the foreach command to get the total number of attacks:
Unset
| makeresults count=5
| fields - _time
| eval attacks_external=10, attacks_internal=1, total=0
| streamstats sum(attacks_external) as attacks_external sum(attacks_internal) as attacks_internal
| foreach attacks_*
[eval total = total + <<FIELD>>]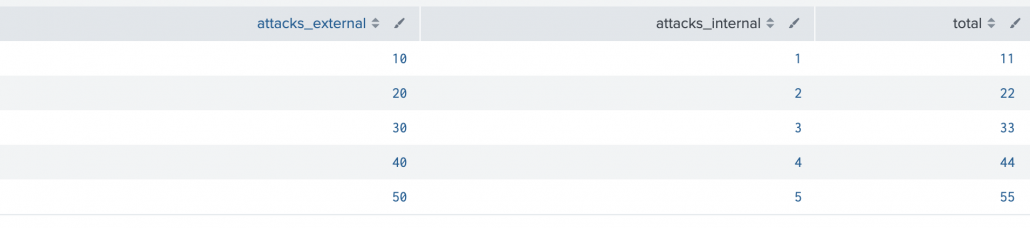
Imagine you don’t know the exact names of the fields starting with the prefix “attacks_*”, but you need to work with them. This is where the foreach command shines. It allows you to efficiently operate on values within fields that share a common prefix, even when the final field names are unknown.
In Splunk 9.x we are able to run foreach over:
- Each field in a wildcard field list, as we saw in previous versions.
- Each value in a single multivalue field.
- A single field representing a JSON array.
Unset
| makeresults
| fields - _time
| eval attacks_external=mvappend("14","33"), attacks_internal=1, total=0
| foreach mode=multivalue attacks_external
[eval total = total + <<ITEM>> + attacks_internal]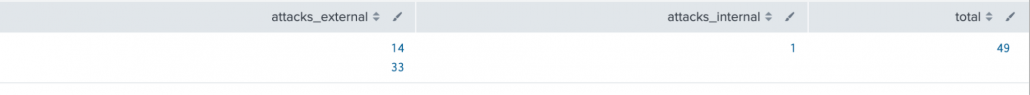
Certainly there are various methods to achieve the same result, and it’s always beneficial to have alternative approaches to compare their performance impact, based on the specific use case. This ensures you avoid costly searches on large databases and prevent memory limit issues. The same principle applies when working with JSON data:
Unset
| makeresults
| fields - _time
| eval attacks_external=json_array("14","33"), attacks_internal=1, total=0
| foreach mode=json_array attacks_external
[eval total = total + <<ITEM>> + attacks_internal]
Field Filters (Preview)
Field filters can help you maintain the confidentiality of sensitive information, such as Personally Identifiable Information (PII) and Protected Health Information (PHI), by modifying visibility during searches executed by non-exempt users, controlling which users can see sensitive data controlled via a simple UI. The filters can either remove fields from the search results or alter the values within these fields. Options for altering field data include redaction, where the field is either deleted or replaced with a predefined string, and obfuscation, where the value is replaced with a cryptographic hash.
By default, this feature is turned off because it is a preview feature, but you can enable it depending on your Splunk Platform:
- Splunk Cloud (>= 9.1.2312): To turn on field filters in your environment, request help from Splunk Support.
- Splunk Enterprise (>= 9.3): According to the documentation you can enable it on your instance, but we tried to apply it on a Splunk 9.2.1 version and it did not work.
An excessive number of field filters will negatively impact the performance of all your searches.
Bitwise Operator
Introduced in Splunk 9.2, the bitwise operator eliminates the need for complicated solutions and complex eval functions to manipulate fields in eval searches to get a bitwise operation. It supports the following bitwise functions:
- bit_and(<values>)
- bit_or(<values>)
- bit_not(<value>, <bitmask>)
- bit_xor(<values>)
- bit_shift_left(<value>, <shift_offset>)
- bit_shift_right(<value>, <shift_offset>)
Bitwise operators are quite useful, especially in fields like computer engineering and cybersecurity, due to their efficiency and low-level control over data. These functions add bitwise functionality directly to the Splunk Search Processing Language (SPL), so you can perform operations such as capture a flag, get the session from some network devices, or apply masks on values without having to use Python workarounds.
One of our customers needed to determine if the sessions from the Palo Alto devices were decrypted by forward proxy. If the sum of a bitwise AND operation on the flags field and the value 0x01000000 is greater than 0 then the session was decrypted by forward proxy. Here is an example:
Unset
| makeresults
| fields - _time
| eval flag = "0x1400000", decrypted="0x01000000"
| eval flag_number = tonumber(flag,16), decrypted_number = tonumber(decrypted,16)
| eval flag_binary = tostring(flag_number,"binary"), decrypted_binary = tostring(decrypted_number,"binary")
| eval result = if(bit_and(flag_number, decrypted_number)>0, "Decrypted by forward proxy", "No decrypted")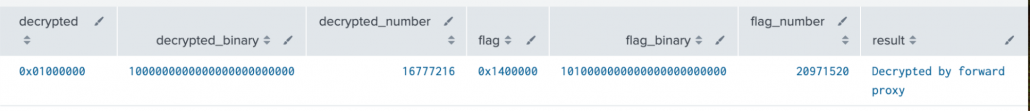
Zero Downtime Upgrades
Are you familiar with this image?

Good news for Splunk Cloud customers in Victoria Experience with Search Head Clusters! From version 9.1.2308, you are able to enhance the high availability journey with Zero downtime upgrades, allowing search continuity for short-running and long-running searches during core upgrades and rolling restarts.
Once the Splunk team performs the upgrade, it will not impact the login sessions, scheduled searches, and indexing, giving you a transparent mode of the upgrade process. Additionally, the status of the process will be present in the Cloud Monitoring Console. The Splunk team is working on reducing the number of disruptive maintenance windows.
Bonus: Search Experience Improvements and Home Page
According to different conversations with the Splunk team during .conf24, the following modifications were implemented:
- Significant enhancements to search process memory management.
- Reduction in search crashes & enhancement of stack stability.
- Faster searches using Parallel Reduce.
- Reduced load time for Search & Reporting app on stacks with many knowledge objects:
- Automotive customer: 8.05s → 3.59s (2.2x speedup)
- Retail pharma customer: 13.66s → 5.59s (2.44x speedup)
- Insurance customer: 18.00s → 8.37s (2.15x speedup)
- Custom bookmarks were added in the Splunk Platform UI Home Page. Additionally, Splunk added custom in-product bookmarks for quick access to guides, manuals, apps, knowledge objects, and other resources.
- The view of recent search history across all apps were consolidated in one place.
References:
https://docs.splunk.com/Documentation/Splunk/9.2.1/SearchReference/Foreach
https://docs.splunk.com/Documentation/Splunk/9.2.0/SearchReference/BitFunctions
https://docs.splunk.com/Documentation/SplunkCloud/9.2.2403/Security/setfieldfilters
Looking to expedite your success with Splunk? Click here to view our Professional Service offerings.
© Discovered Intelligence Inc., 2024. Unauthorized use and/or duplication of this material without express and written permission from this site’s owner is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to Discovered Intelligence, with appropriate and specific direction (i.e. a linked URL) to this original content.