Splunk Asset and Risk Intelligence – a CAASM Solution for Splunk
At the recent Splunk .Conf in Las Vegas a couple of weeks ago, we were able to get a detailed demo of Splunk’s new and exciting Splunk Asset and Risk Intelligence (Splunk ARI) security solution. What a great solution and one that is much needed within their security solution portfolio. Splunk ARI falls into a category of products known as CAASM – Cyber Asset Attack Surface Management. In this post, we dive a little deeper into what CAASM is, why it is critical tool for your organization and how Splunk ARI can help.
In security operations, there has been a recent and rapid increase in the adoption of Cyber Asset Attack Surface Management (CAASM) solutions. With ever changing technology, cloud use and changes in employee working environments (remote, hybrid, in-office), there is a growing need for tracking, monitoring and managing assets and identities.
We recently came across some great informative articles, published by Gartner and LevelBlue, which outline important benefits and functionalities of CAASM solutions. We pulled some of the key concepts from these articles and look at how Splunk ARI addresses them.
Asset Records
Highlighted by both articles is the importance of complete asset records, which Gartner stated as “owned assets, identities, applications, 3rd party SaaS, IaaS and PaaS”, and LevelBlue simply described as “complete asset coverage” while also indicating the importance of “mean time to inventory”. The only way to effectively manage an attack surface is to ensure you have the complete and up-to-date information for your attack surface.
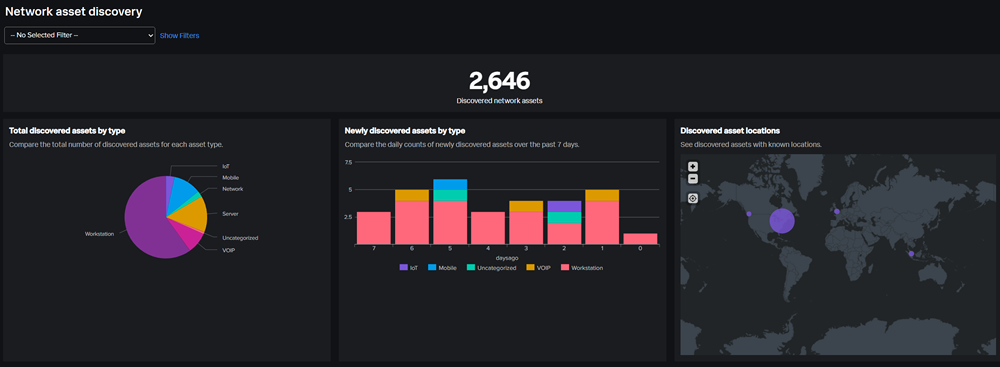
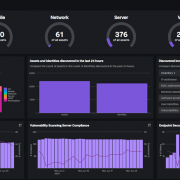
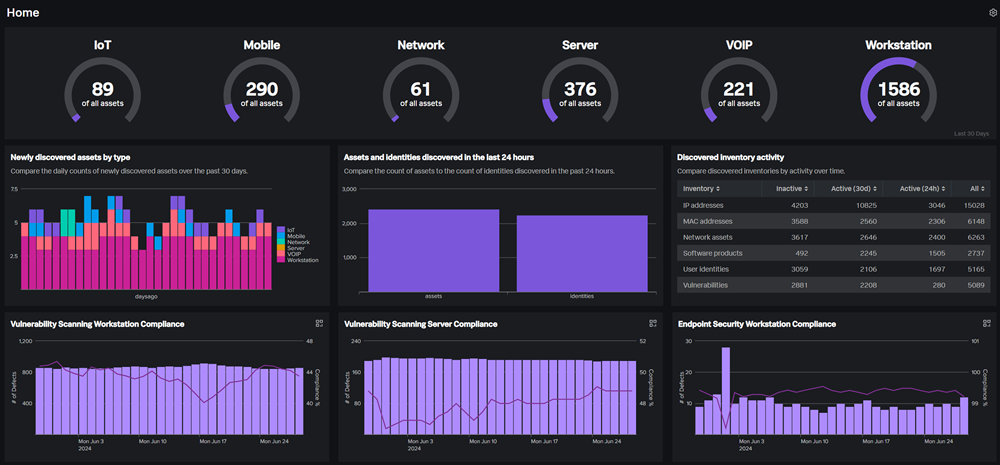
Splunk ARI uses your existing data sources that you have within Splunk and any other sources, to continuously discover active assets and identites on the network. By pulling all of these data sources together and working its magic, Splunk ARI is able to produce astonishingly accurate and complete asset records, that update over time, so your data never gets stale.
Vulnerability Awareness
Both articles indicated that an effective CAASM would have asset vulnerability awareness and management features as well as improved vulnerability mitigation speed.
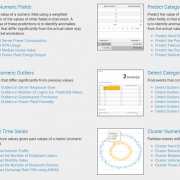
Splunk ARI integrates with your vulnerability scanning tools and correlates this with asset data to identify discovered assets with vulnerabilites, highlight these vulnerabilities when performing security investigations and to report on vulnerability scanning gaps across your network.
Compliance Reporting
Both articles address the importance of compliance reporting features, to ensure assets follow regulatory requirements and are managed to the appropriate standard, which will then decrease the likelihood of experiencing a security incident.
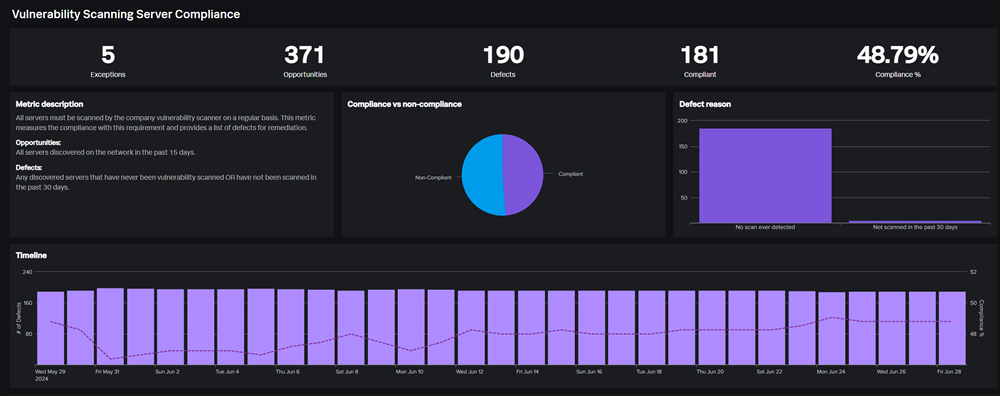
Splunk ARI allows you to quickly add cybersecurity metrics to measure compliance across many different security controls. For example, identity discovered assets that are not in your CMDB, assets that have no endpoint security or assets that have never been vulnerability scanned. As the asset records within Splunk ARI are continously updated, these metrics report on compliance in real-time. This means that as identified security control gaps are addressed, the metrics will update accordingly.
Finding the Right CAASM Solution
While selecting the right CAASM solution for your organization can seem a bit daunting, Gartner made a recommendation to look into what existing solutions are offered by your current technology providers, which will provide you with some cost savings as well as simplified implementation and usability.
If you are using Splunk today, then implementing Splunk ARI is a great choice and offers powerful functionality and features. Note that Splunk ARI is a standalone solution for Splunk and Splunk ES is not required. For those with Splunk ES, then Splunk ARI is a perfect complement and the accurate and complete asset and identity records discovered by Splunk ARI can populate the A&I Framework within Splunk ES.
Splunk ARI is available now as part of their Early Access program and is expected to be generally available very shortly.
References:
The Growing Importance of CAASM in Company Cybersecurity Strategy – LevelBlue
Innovation Insight: Attack Surface Management – Gartner
© Discovered Intelligence Inc., 2024. Unauthorized use and/or duplication of this material without express and written permission from this site’s owner is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to Discovered Intelligence, with appropriate and specific direction (i.e. a linked URL) to this original content.